 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
Gene therapy offers unique possibilities to treat the _______ causes of diseases.
A.genetic
B.environmental
C.emotional
D.dietary
 如果结果不匹配,请 联系老师 获取答案
如果结果不匹配,请 联系老师 获取答案
 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
A.genetic
B.environmental
C.emotional
D.dietary
 如果结果不匹配,请 联系老师 获取答案
如果结果不匹配,请 联系老师 获取答案
 更多“Gene therapy offers unique pos…”相关的问题
更多“Gene therapy offers unique pos…”相关的问题
A.have a surgery
B.cure an illness
C.return to active life
D.meet a challenge
A.WAN B.LAN C.VPN D.VAN
The five primary modes of transportation are rail,road,pipeline,water,and air. Each has different economic and service characteristics.【B1】offers the cost—efiective,energy—efficient transport of large quantities of goods over long distances.【B2】offers more flexibility and versatility to the shipper than virtually any other forms of transportation.【B3】are primarily used to move petroleum,natural gas,and chemicals.For suitable commodities,pipelines are the most efficient mode of transport.They offer a closed system with little risk of loss or damage to the products moved and extremely low cost.The most expensive of all the modes,【B4】offers the fast service but at a relative high price.【B5】 occurs on inland waterways and oceans.Though slower than other modes,this form. of movement is also relativelv inexpensive.
【B1】
A.Rail transport
B.Road transport
C.Truck transport
D.Air transport
根据以下资料回答 41~45 题
The five primary modes of transportation are rail, road, pipeline, water, and air. Each has different economic and service characteristics. (41 )offers the cost -effective, energy- efficient transport of large quantities of goods over long distances. (42 )offers more flexibility and versatility to the shipper than Virtually any other forms of transportation. (43 ) are primarily used to move petroleum, natural gas, and chemicals. For suitable commodities, pipelines are the most efficient mode of transport. They offer a closed system with little risk of loss or damage to the products moved and extremely low cost. The most expensive of all the modes, (44 ) offers the fast service but at a relative high price. (45 )occurs on inland waterways and oceans. Though slower han other modes, this form. of movement is also relatively inexpensive.
第 41 题
A.Rail transport
B.Road transport
C.Truck transport
D.Air transport
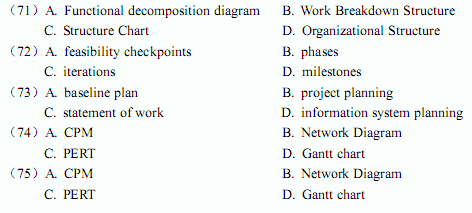
A project management technique that is currently in widespread use is the(71) . The purpose of this technique is to detail, in hierarchical fashion, all of the activities that are required to meet project objectives. There are some special activities called(72) , which are events that signify the accomplishment or completion of major deliverables during the project. Most system development methodologies also provide(73), whose purpose is to contain the various pieces of relevant information-feasibility assessments, schedules, needs analysis, and so forth-in a single place so that they can be presented to project clients and other related parties. Several types of important network diagrams are used in project management.(74) was developed to make clear the interdependence between project tasks before those tasks are scheduled.(75) offers the advantage of clearly showing overlapping tasks.
A.Structure Chart
B.Organizational Structure
C.Work Breakdown Structure
D.Functional decomposition diagram
A project management technique that is currently in widespread use is the(71). The purpose of this technique is to detail, in hierarchical fashion, all of the activities that are required to meet project objectives. There are some special activities called(72), which are events that signify the accomplishment or completion of major deliverables during the project. Most system development methodologies also provide(73), whose purpose is to contain the various pieces of relevant information - feasibility assessments, schedules, needs analysis, and so forth - in a single place so that they can be presented to project clients and other related parties. Several types of important network diagrams are used in project management.(74)was developed to make clear the interdependence between project tasks before those tasks are scheduled.(75)offers the advantage of clearly showing overlapping tasks.
A.Structure Chart
B.Organizational Structure
C.Work Breakdown Structure
D.Functional Decomposition Diagram
()阅读下列说明和C语言程序,将应填入 (n)处的语句写在答题纸的对应栏内。[说明]设有定义 #define ITEM struct item #define SIZE sizeof(ITEM) ITEM { int num; ITEM *next; }; ITEM *head=NULL; 下述函数定义实现按插表尾形式(即每一新表元素插入至当前所生成链表的表尾之后)生成一个正向线性链表。最后指向所生成链表表头的指针作为函数值返回。为生成一个线性链表,要求输入一批整型数据,并以-1作为结束标志。请填空完善程序。 ITEM *gene(ITEM *head) { ITEM *temp,*tail;/*tail指向当前链表尾结点*/ int intno; printf("Enter integer NO.,-1 to stop:\n"); scanf("%d",&intno); while (intno!=-1) { temp=(____(1)_____)malloc(SIZE); temp->num=intno; if (head==_____(2)_____) /*空表*/ { head=temp; tail=______(3)______; } else /*非空表*/ { ____(4)_______=temp; tail=temp; } scanf("%d",&intno); } return (_______(5)_______);
Public Key Infrastructure(PKI) service providers offer organizations fully integrated PKI-managed services designed to secure Intranet, Extranet, Virtual Private Network(VPN), and e-commerce applications. PKI solutions can enable a number of security services, including strong authentication and non-repudiation of transactions.eToken enables the users of PKI systems to generate and store(101)and digital certificates inside the token, creating a secure environment and allowing full portability and maximum ease of use. eToken Pro can also perform. sensitive on-chip(102)operations, ensuring that users' keys axe never exposed to the PC environment, eToken eliminates the need to store(103)and keys on a hard disk or browser file, or to transmit them across the Internet/Extranet; assuring peace-of-mind and confidence during online communications.A digital signature is created using the private key of an individual to ensure the Validity of his request. This technology can be used to guarantee(104)of various transactions. The strength of either the authentication level or the digital signature relies on the level of protection offered to the private key. eToken Pro offers the maximum level of security, since it enables the use of the private key for signing and authenticating inside the eToken.The most secure use of authentication involves enclosing at least one certificate with every signed message. The message(105)verifies the certificate using the CA's public key. If the sender's public key is legitimate, the recipient verifies the message's signature. Digital signatures created with a private key are verified with the digital certificate containing the public key.
A.private keys
B.public keys
C.authentication codes
D.message digests